Cloud-native technologies are on a trajectory to take over modern application architecture. A cloud-native approach includes leveraging technologies such as containers, microservices, service meshes, declarative APIs, and immutable infrastructure to allow IT organizations to build and deploy scalable applications in an environment-agnostic fashion. Cloud-native applications can be deployed anywhere: public cloud, private cloud, hybrid cloud, and on-prem infrastructure.
Palo Alto Networks this month stepped up to address AppSec concerns around cloud native security with a new set of CI/CD security capabilities for its Prisma Cloud offering. Let’s go deeper on what was announced and why it’s important.
Cloud Native Adoption & Security Concerns
Every year the Cloud Native Computing Foundation (CNCF) releases an industry-wide survey detailing the adoption of cloud-native technologies across a range of organizations. In its most recent survey, the CNCF found that while nearly 80% of respondents use containers in some fashion (foundational to cloud-native), only 30% of organizations have adopted cloud-native approaches across almost all development and deployment activities.
Cloud-native may be the future, but there are obstacles that temper adoption. The same CNCF survey revealed that the two biggest challenges to cloud-native adoption are training and security. In organizations that fully embrace cloud-native, security is the topmost challenge.
This concern dovetails with rising threats to the software supply chain. According to recent numbers from Sonatype’s annual State of the Software Supply Chain report, attacks on the software supply chain have impacted 61% of businesses in the United States. It also shows that there has been an astonishing 742% average annual increase in software supply chain attacks over the past three years.
CI/CD Security by Prisma Cloud
In response to the rising adoption of cloud-native technologies, and the associated security risks, the industry has adopted an approach to cloud-native security called CNAPP – cloud-native application protection platform. CNAPP simplifies the monitoring and security of cloud-native applications by unifying multiple disparate security capabilities to protect the full lifecycle of cloud-native applications.
Palo Alto Networks brings CNAPP to life by introducing new CI/CD security capabilities into its flagship Prisma Cloud offering. The new CI/CD security capabilities provide an integrated and unified view of an organization’s entire cloud-native pipeline, allowing for unmatched visibility and protection for a cloud-native engineering ecosystem.
Unified Application Security Dashboard
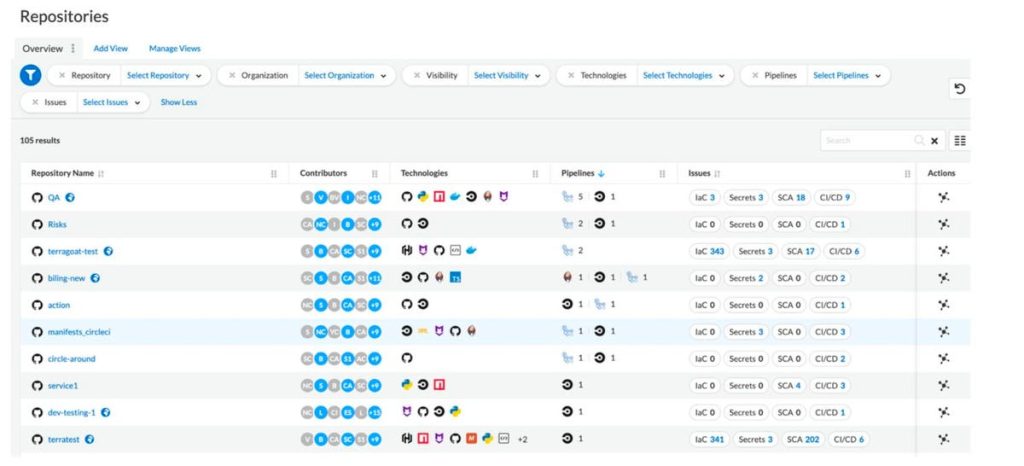
One of the biggest challenges of managing any IT infrastructure is the ability to simply see what’s happening. This problem is amplified in the cloud-native software development world, where code is managed across a range of systems with a range of system-specific security scanners while often relying on upstream packages that are out of your control. Prisma Cloud addresses this with its new Application Security Dashboard.
The Primsa Cloud Application Security Dashboard provides a unified view of an organization’s cloud-native engineering ecosystem. The dashboard normalizes signals from the code scanners already in use to provide a centralized view of risk and a trending view that shows security performance across development teams.
With the new CI/CD security features, Prisma Cloud now gives AppSec teams a single-pane-of-glass view across code repositories, contributors, technologies used, and the connected pipelines. Teams can more easily prioritize risks with a complete infrastructure view that fully understands which code repositories and pipelines are connected to production systems. It’s a really nice capability.
Attack Path Analysis
Graph databases are designed to derive and understand relationships between multiple pieces of data. In the cybersecurity world, graph databases allow for rapid, simultaneous correlation between multiple signals to quickly identify threats and map the pathway of an attack. The Prisma Cloud Application Graph is an ideal example of using graph database technology to enhance the security of cloud-native pipelines.
The Prisma Cloud Application Graph analyzes the entire ecosystem, correlating disparate signals across codebases, scanners, and orchestration and automation tools to provide centralized visibility and control across workflows. This allows AppSec teams to untangle often-complex relationships to pinpoint risks and understand the breach pathways to critical assets.
The dynamic view across the engineering ecosystem allows administrators and AppSec teams to better understand and analyze the environment. This is a crucial capability for cloud-native delivery.
Analyst’s Take
Palo Alto Networks is investing aggressively in technologies to secure the cloud, all delivered as part of Palo Alto’s Prisma Cloud offering. This latest update extends those capabilities to include securing the cloud-native workflows that underpin modern application delivery.
Securing the software supply chain is a foundational step in application security. The powerful capabilities of cloud-native technologies are changing how applications are built and deployed. At the same time, the nature of the process opens the door to malicious exploits. Indeed, the number of attacks on cloud-native applications is rapidly growing.
Securing an infrastructure, whether physical or cloud-native, starts with simplifying the process. Palo Alto Networks does this with its unified CI/CD security approach, bringing together not just Palo Alto’s security technology but also integrating the scanners that DevOps teams are already using. As simple as this sounds, it’s incredibly powerful.
Disclosure: Steve McDowell is an industry analyst, and NAND Research an industry analyst firm, that engages in, or has engaged in, research, analysis, and advisory services with many technology companies, which may include those mentioned in this article. Mr. McDowell does not hold any equity positions with any company mentioned in this article.
Read the full article here